Going from an "A" to an "A+" on ssllabs.com
Previously I got docker working with nginx and let’s encrypt; this resulted in an “A” from ssllabs.com. Let’s see about getting that to an “A+”.
As a baseline here’s what I’m currently working with from SSL Labs:
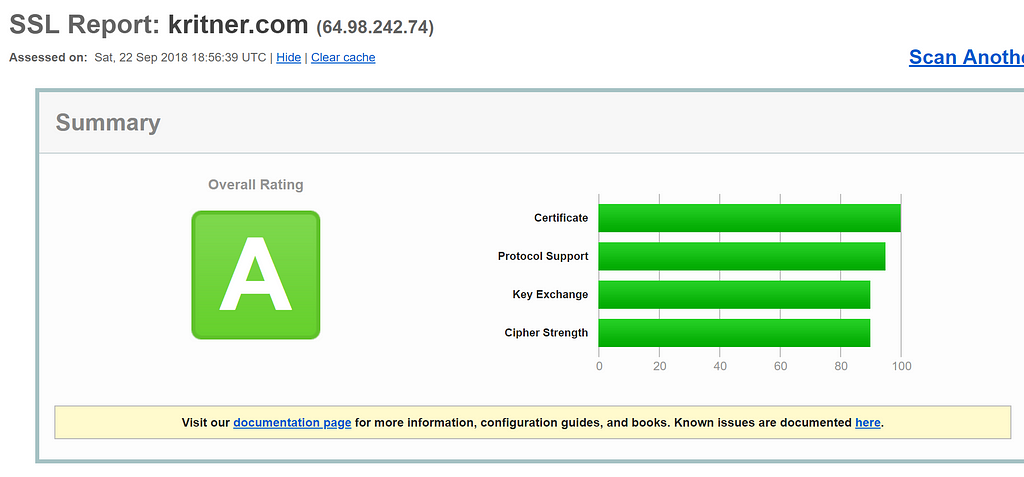
An “A”, not terrible. This is the first time I’m really going through this report, not really sure what should keep an eye on, but let’s take a look.
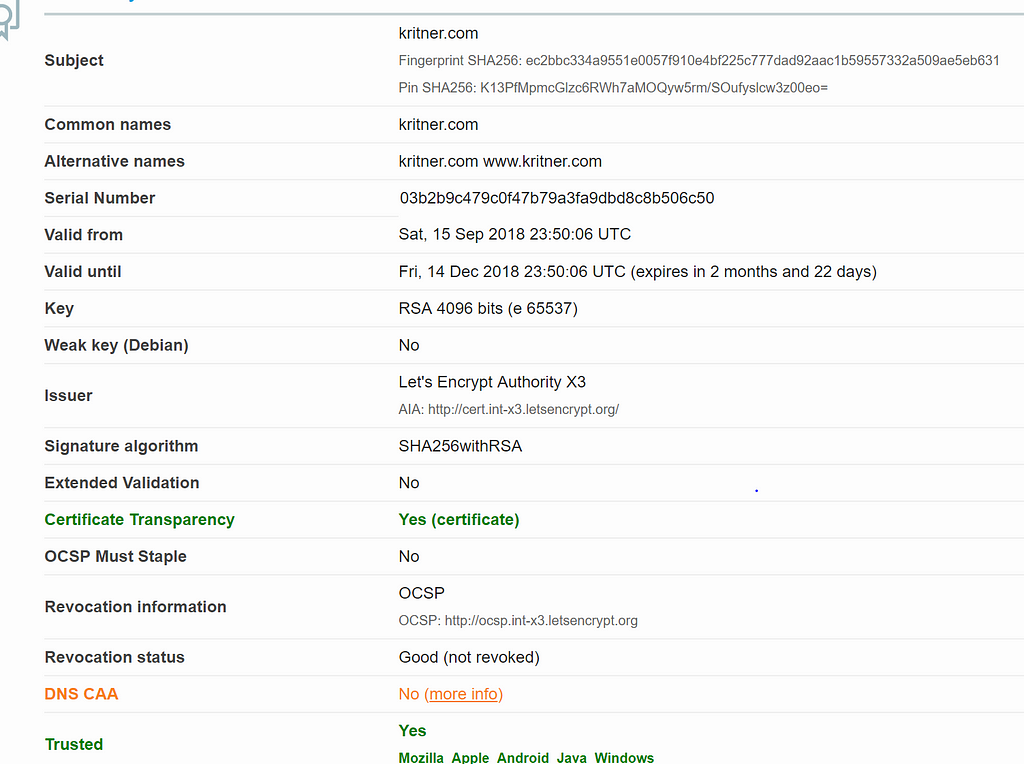
Green and yellow — this seems promising! “more info” under DNS CAA points me over to https://blog.qualys.com/ssllabs/2017/03/13/caa-mandated-by-cabrowser-forum — tldr seems to be add a record through your DNS that whitelists specific CAs, in my case let’s encrypt.
I use DNSimple as my DNS, and it was pretty straightforward to add the record (and I’m doing this as I type, so hopefully I don’t screw it up!).
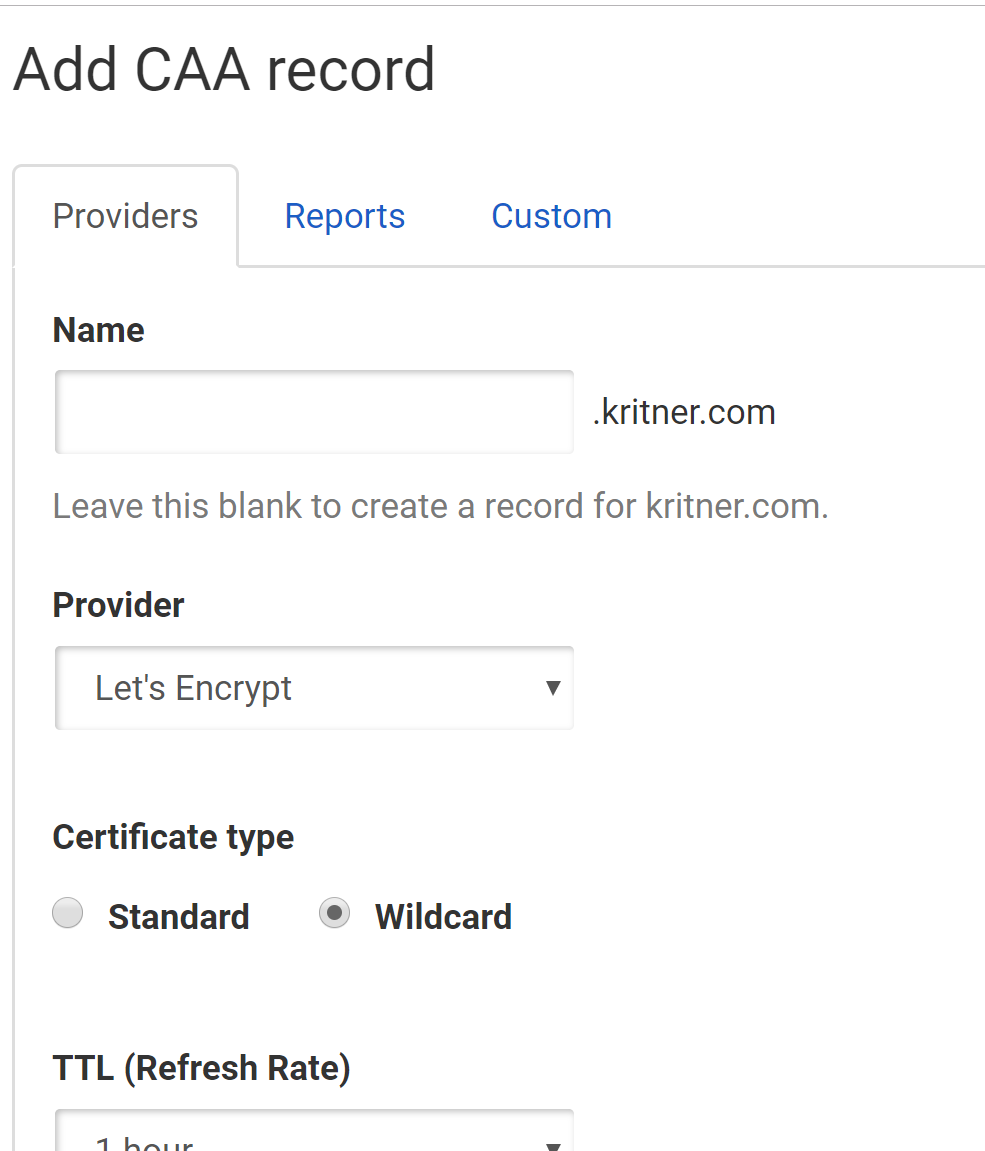
Okay, so the CAA record is taken care of, let’s see what else is going on in the SSL Labs report…
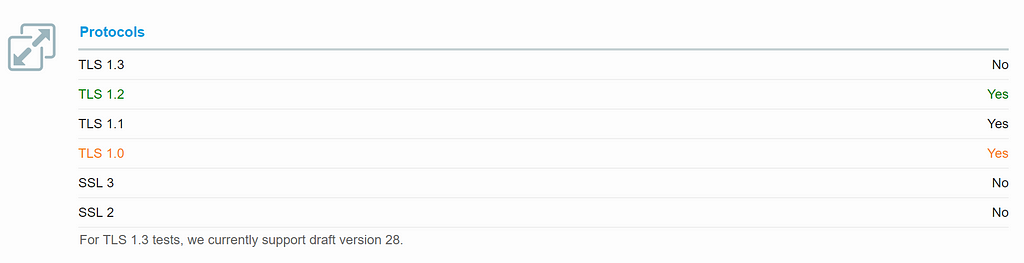
TLS and SSL are different methods of accomplishing HTTPS, TLS being the successor to SSL. From the looks of this, it’s a good thing my site supports TLS 1.1 and 1.2, a bad thing it supports TLS 1.0, and a good thing all flavors of SSL are not supported. TLS 1.0 being a bad thing to support makes sense — since it was end of lifed on 2018–06–30.
A large remainder of the warnings in the SSL Labs report seems to be centered around the fact that TLS 1.0 is supported:
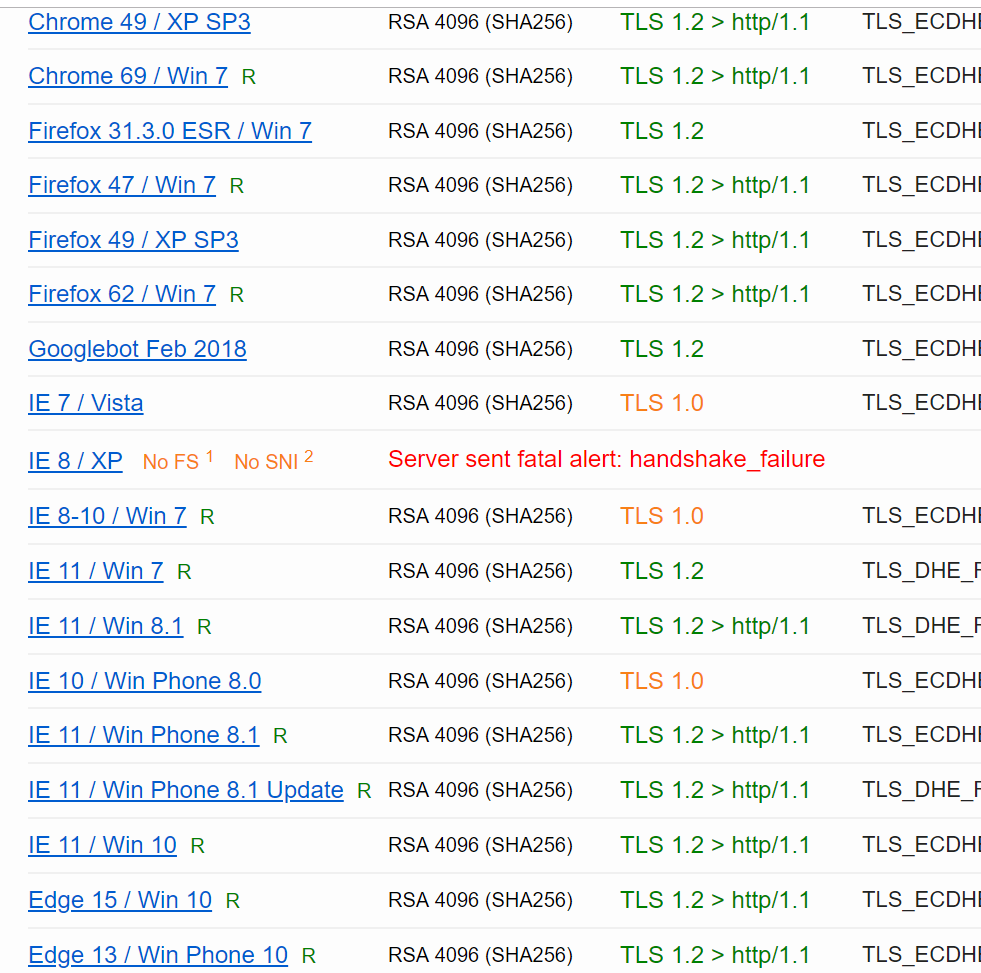
So let’s see about getting TLS 1.0 disabled through my nginx config.
Nginx Updates
I recalled an “ssl.conf” file from the mapped volume in the previous post — though I had not made any changes to it up to this point. Since I will likely need to make changes to this file (it makes sense that SSL related settings would be here, no?), I will be adding this file to a new docker volume; so I can check in changes to the file.
A snippet of my original docker-compose file:
1 | |
The new addition to the volumes portion of the file:
1 | |
This will allow my ssl.conf file to be mapped within the docker container, overwriting the original image’s ssl.conf; no API keys, passwords, etc in this file, so might as well keep its changes in source.
The entire docker-compose file now looks like:
1 | |
Next, onto the ssl.conf itself. The original ssl.conf is:
1 | |
This all seems pretty standard and simple to figure out. Under “protocols” you can see there is a TLSv1 listed, which we’ll be removing. There is also a commented out line regarding HSTS, and I can’t really think of a reason to keep that disabled. Those two changes make the entire file look like:
1 | |
I think that’s pretty much everything — we added a CAA record, disabled TLSv1, and made a few modifications to support the TLS change in our docker-compose file.
Let’s see what SSL Labs thinks now:
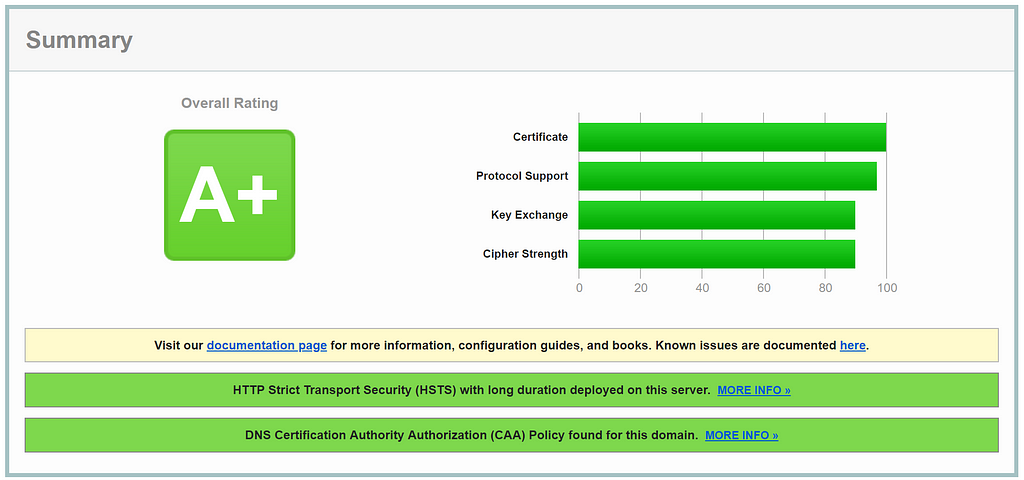
Woohoo! A+! Here’s the GitHub PR related to changes.
Related:
Going from an "A" to an "A+" on ssllabs.com

